What All Nonprofits Need to Know about Cybersecurity
Regardless of your level of technical expertise, you’ve probably heard the term cybersecurity.
And if you haven’t made it a priority yet, now is the time to start.
Hackers continue to become more sophisticated. It’s imperative to make online safety a top priority for your nonprofit to protect both your work-related information and the personal information of your supporters. To equip you with knowledge and actionable advice, Ekin Sisli, Director of Systems Engineering at Flipcause, is sharing what all nonprofits need to know about cybersecurity.
In the physical world, keeping yourself and your belongings secure is a fairly obvious task: you can lock your front door or the doors to your car. You make sure never to leave your belongings unattended in a public place. Even your debit card requires a pin for use at the ATM or grocery store—and you keep that number a secret. You employ a number of habits to ensure that you stay safe out there in the world.
But what about online?
Now more than ever, we rely on our devices and the internet to connect to the outside world. So it’s important to be aware of the risks involved and take steps to keep our information protected, just as we do with our physical possessions.
Here’s a list of steps to take to keep your nonprofit safe online:
1. USE strong passwords
Your passwords are the first layer of protection for all of your accounts. And while it may be easier to come up with a simple password that you can remember and then use over and over, doing so makes you a target for hackers. If they’re able to figure out that single password, they can access all of your personal information. Just like you have different keys for different doors, you want to make sure that all of your accounts have different passwords.
To keep your accounts secure:
Use a unique password for each login.
- Don’t reuse passwords across accounts; while it’s easier for you to remember, it’s also easier to hack – it’s like giving a stranger the keys to your entire house.
Create passwords that are long and complex.
- When hackers “guess” your password, it’s usually a result of sheer computing power.
- Did you know “password” and “1234567” are the #1 most commonly used passwords? Those are the first they will try.
- This means that both the length and complexity of your password are important. A strong password is at least 15 characters long. Many sites now have specific requirements for your password, but they should always contain an upper and lowercase letter along with special characters whenever possible.
- Avoid using dictionary words in your password. The tools being used to break passwords are becoming more sophisticated and include repositories of dictionary words in multiple languages.
Don’t write your passwords down on paper.
- It can be tempting to scribble your password in your notebook or leave it on a post-it note on your computer. But doing so makes your accounts vulnerable! It’s like leaving the key to your front door on a hook outside or under the mat; any passerby can easily use it access your account.
Start using a password manager.
- Since the safest passwords are pretty much impossible to remember, you should automatically generate and store your passwords using a password manager. This way you only have to remember the password to a single account. There are both free and paid accounts, and it’s a good idea to require everyone at your organization to use one.
2. Use two-factor authentication (2FA) EVERYWHERE possible
Using two-factor authentication is one of the most important steps you can take to secure your accounts.
Two-factor authentication requires you to verify your identity not just with a username and password, but also with something that you have on you, like your cell phone. When you enable two-factor authentication, even if someone has your login information, they won’t be able to get into your account unless they also have access to your second method of verification. After entering your username and password, you’ll receive an additional verification code to enter while logging in. You can choose to receive SMS messages for two-factor authentication, or get your code through an app like Google Authenticator (which is even more secure). Some accounts may automatically prompt you to set up two-factor authentication, but sometimes you need to go into your security settings to enable it. Even though scammers keep getting more sophisticated in their ability to get your login credentials, two-factor authentication continues to be a silver bullet, and according to Microsoft, prevents 99% of hacker attempts.
You should turn on two-factor authentication:
- Everywhere you can.
- Especially with email, financial accounts, document management and database applications, and linked accounts, such as Facebook.
- If you use Google or Facebook to link to other accounts for sign-in, be sure these other accounts also have extra secure passwords in addition to 2FA.
3. Avoid using public wifi
Using free public wireless networks to access the internet on your computer or cell phone can put you at risk. Public networks are vulnerable because hackers break into or imitate them, executing what are called “man-in-the-middle” attacks. These kinds of attacks enable them to see your activity and steal your data while you access the internet.
To keep yourself safe from this type of attack:
Use a personal hotspot via your cell phone if available.
- This is the safest way to access the internet outside of the office. Make sure that you have a strong password in place and that you don’t share it with others.
Only connect to public wifi as a last resort.
- It’s common for hackers to spoof fake public free wifi. Fake public networks will often have names that are very similar to the real network, like “NYLibrary” instead of “NYPL”.
- If you have to use public wifi, always confirm with the provider to make sure you have the correct network name and what information is required for login.
- Delete public networks from your wifi list on your computer after using them.
Use a virtual private network (VPN) to encrypt your connection and anonymize your activity.
- You’ll install an application on your computer and activate it whenever you’re connecting to a public wifi network. When you’re connected to the VPN, it’s not possible to connect your internet activity with your computer’s IP address. This makes it significantly harder for hackers to piece together your identity and steal your information.
- Using a free VPN isn’t recommended unless you’ve vetted it heavily; for a small fee, you can install NordVPN or ExpressVPN. It’s worth the fee to keep your data protected.
4. Secure your computer and cell phone number
In addition to securing your online accounts, you’ll also want to protect your devices. Your computer is a valuable asset, and hackers can steal your phone number to impersonate you and access your accounts.
To keep your phone and computer secure:
- Make sure your login to your work (and home) computers have a long, complex password that is unique from other passwords you use.
- Never leave your computer unattended anywhere, even in the office.
- Make sure your phone lock has an extra secure passcode.
- SIMs get hacked and phones get stolen. Set up a special PIN on your phone number via your cell provider (this is different and additional to your online login password for managing that account).
- Never give out your phone number unless you absolutely need to. The number itself is a code that can be used to verify your identity and accounts.
5. Find out if you’ve been part of a data breach
Security breaches can have big consequences: you don’t want anyone impersonated you or your nonprofit online. And you also don’t want to wait until something bad happens to find out that your data has been compromised.
You can proactively make sure that your data is safe by:
Searching your personal and work emails at https://haveibeenpwned.com/.
- This will tell you if your email address was found in a data breach and on the dark web.
- If you do find out that your data is compromised, you’ll want to change your password right away.
6. Avoid phishing scams
A phishing scam is when someone pretends to be a reputable agent or company to steal your personal information. It might be someone pretending to be your HR manager or boss, your bank, or even the IRS. These scams use social engineering tactics such as fear, urgency, and authority to make you feel like you have to give them your information.
Examples include voicemails on your phone saying that you owe money to the IRS, or even text messages saying your Google email has been compromised and you need to enter a new password.
To avoid phishing scams:
Slow down and verify before clicking anything or responding to phone calls/text messages.
- Is the message sent from a company email address? Do you know who the person is? Bad grammar is a dead giveaway!
- Always check the actual sender of the email to see if it comes from who it says it is.
- Mouse over links in the email (but don’t click them) to reveal if the URL is what it says it is.
- If you receive text communications from Google, they won’t come from a phone number with an area code.
- Even if the communication seems legitimate, go directly to the actual website to log in, rather than using links provided within the email or text message.
Only enter personal information on sites served over HTTPS.
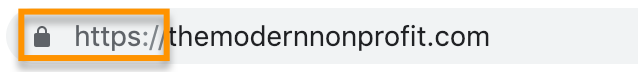
- You’ve seen the “http” at the beginning of every web address. These letters stand for HyperText Transfer Protocol and tell machines how to send information on the internet.
- This protocol has been updated to encrypt the information being transferred, so many URLS now read “https.” That extra “s” at the end stands for Secure, and lets users know that their data will be protected when they enter it through sites that use this new protocol.
- Many browsers will automatically warn you if a website is insecure, but you should verify that the URL is preceded by https:// in your browser, as in the picture above, before entering your personal information on a website.
- Keep in mind, hackers can buy security certificates, too. So, HTTPS and a green lock showing don’t alone prove that the website is legitimate, but a lack of HTTPS is a dead giveaway that inputting any sensitive information into this site is unsafe!
7. Keep your software and devices updated
Always keep your phone, tablet, computers, programs, and apps completely up-to-date with current software. Software companies are constantly working to ensure that you’re safe when using their technology, and patching security vulnerabilities as they uncover them.
Install software updates as soon as they’re available.
- Updates often fix security vulnerabilities, which change over time as hackers become more sophisticated.
- You should also search in your device settings to see if any new software updates are available.
8. Make cybersecurity company policy
Take the time to make sure everyone at your organization is using these best practices to stay safe online. Because so much of our data is shared across accounts, it only takes one person’s outdated phone software to compromise everyone else’s information.
In addition to the other recommendations above, it’s important to:
Actively manage user permissions across shared accounts.
- In your database, restrict access to files for each person who will sign in and access the data. People should only have access to the information they need to get their job done.
- If you use a shared file system in the cloud, like Google Drive, set permissions so that users only have access to the folders they absolutely need.
- Don’t forget to terminate permissions once staff leave! Create an offboarding checklist, and plan to do a quarterly permissions audit to remove access for anyone who no longer needs it.
Teach your staff to stay safe online.
- Create an internal document that outlines policies for cybersecurity and share it with staff.
- Dedicate time to discussion and training. Make cybersecurity training part of your onboarding process for everyone at your organization.
We want to make sure you and your nonprofit are completely secure online. If you have any questions about the recommendations above, please get in touch with us in the comments!
Ekin Sisli is the Director of Systems Engineering at Flipcause. He has worked in IT leadership roles at multiple nonprofits, including the Mother Child Education Foundation and the Green Thought Association in Istanbul, Turkey. Ekin is a world citizen and polyglot, having lived in Turkey, Italy, Brazil, Japan and now the US—learning each native tongue in addition to multiple programming languages.


0 Comments